I want to automate adding my custom certificates in 9.6.x (and later 25.x). I’ve found references to older versions of Integrity for file locations but have they changed in 9.6.x? If so, which directory?
Solved
Automating custom certificates in 9.6.x
Best answer by bshorland
PUT https://{{bamip}}/api/v2/settings/10Payload (redacted private key)
{
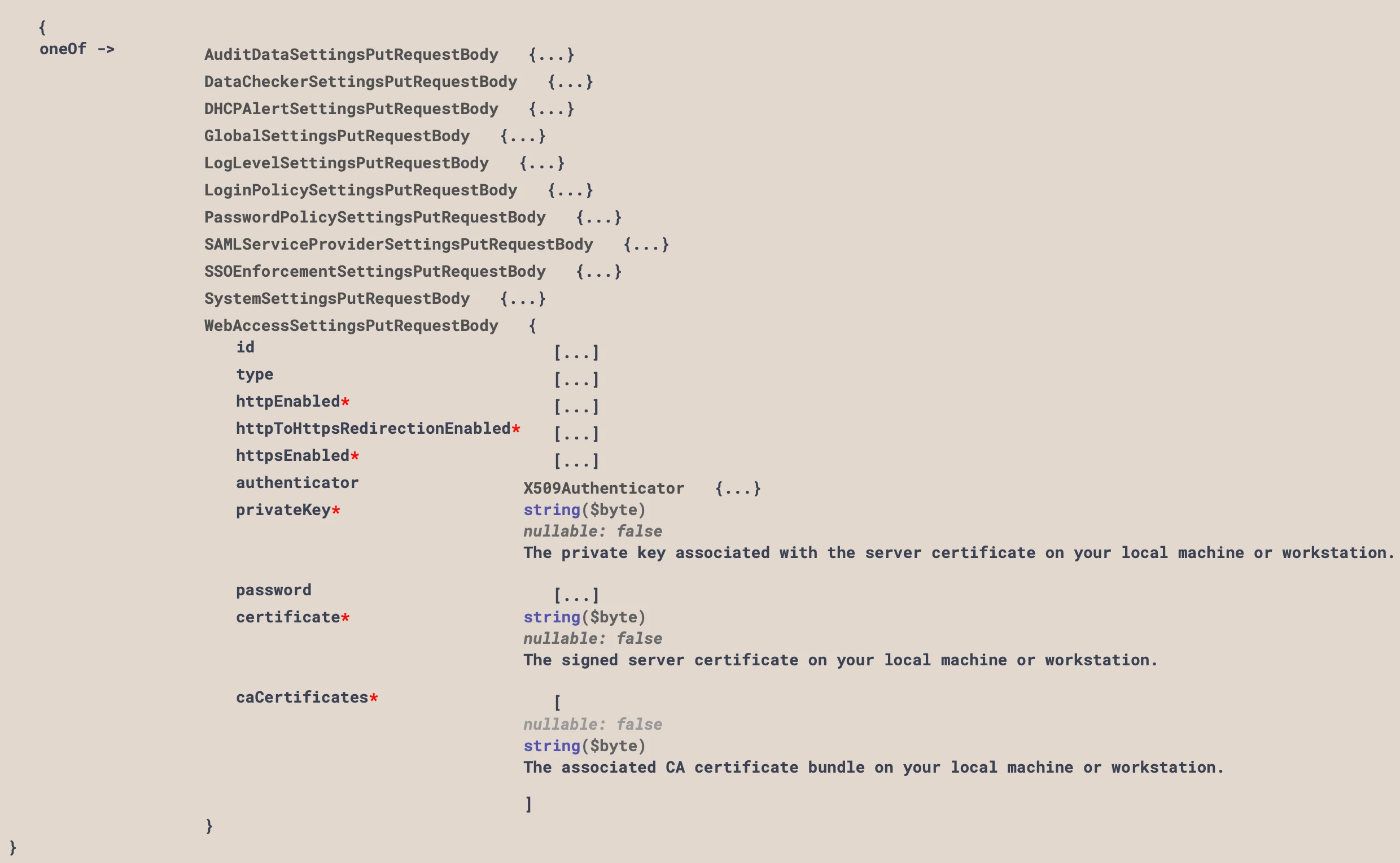
"type": "WebAccessSettings",
"httpEnabled": true,
"httpToHttpsRedirectionEnabled": false,
"httpsEnabled": true,
"authenticator": null,
"privateKey": "<REDACTED>",
"certificate": "MIIG/zCCBOegAwIBAgIQCEdSum9NVH8fTjpaPZBTsjANBgkqhkiG9w0BAQsFADBxMQswCQYDVQQGEwJVUzErMCkGA1UEChMiVml0YWx3ZXJrcyBJbnRlcm5ldCBTb2x1dGlvbnMsIExMQzE1MDMGA1UEAxMsVml0YWx3ZXJrcyBJbnRlcm5ldCBTb2x1dGlvbnMsIE5vLUlQIFRMUyBJQ0EwHhcNMjUwNjA3MDAwMDAwWhcNMjYwNjA2MjM1OTU5WjAZMRcwFQYDVQQDEw5iYW0xMC5kZG5zLm5ldDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOEjiLgOgDh4cQcgHIZTGD3/RUEGTlULqVyOQxN8JmiQxTVwJTDOjYluqRu3WIdqFMhOrYfpaAp9gfxsnMVGoJrUEnS56aN84YOmCwrtpRsM0rXgHISG2n9N7R98At/s65KJA/DTCFKsvREm/smt8K85/0Yeq0I9TtegYH2aBU/q0fWCeEFGETaTy5Us7RTIsXrWsWA8B4dy0sUybGWRnRD31MF8KxD+byOwY9fnaFWsm2OmGKWVWOGDQ07fKyCnx1hUY5bwWQ/9oKMX5bWE0yLSWvZ18N23/3Yj1QoAUC8eHCcrJPhmJknHL6sRB7yLpyEtXA0xmKVGcEyVSkW8YSMCAwEAAaOCAukwggLlMB8GA1UdIwQYMBaAFBHqPdsoV2Pcwk4udmsY7C/7qiycMB0GA1UdDgQWBBRe3LoT7X3RV1x4e9VxFT3fOJkb+jAZBgNVHREEEjAQgg5iYW0xMC5kZG5zLm5ldDA+BgNVHSAENzA1MDMGBmeBDAECATApMCcGCCsGAQUFBwIBFhtodHRwOi8vd3d3LmRpZ2ljZXJ0LmNvbS9DUFMwDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjCBiAYIKwYBBQUHAQEEfDB6MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wUgYIKwYBBQUHMAKGRmh0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9WaXRhbHdlcmtzSW50ZXJuZXRTb2x1dGlvbnNOby1JUFRMU0lDQS5jcnQwDAYDVR0TAQH/BAIwADCCAX4GCisGAQQB1nkCBAIEggFuBIIBagFoAHUADleUvPOuqT4zGyyZB7P3kN+bwj1xMiXdIaklrGHFTiEAAAGXSwypbAAABAMARjBEAiArFPtnEXFmXoQZPrqAfJiNoxEIgZLZgH1ldBp5YVo7OgIgEQ0sOWnhJV1OB3/Uspmjl8a8wNgkqH/Pf0yengqcDq0AdwBkEcRspBLsp4kcogIuALyrTygH1B41J6vq/tUDyX3N8AAAAZdLDKmqAAAEAwBIMEYCIQDziFWdp5ZYzhfyMrwm1+/6zqOm3fPRGcm2uXbHYkeDxgIhAOwYEC0uH828jjZagOR3igFh9By7idk49G/Rw74jUbvOAHYASZybad4dfOz8Nt7Nh2SmuFuvCoeAGdFVUvvp6ynd+MMAAAGXSwypvAAABAMARzBFAiEAkVlAFNKxAcVYRKYFn4qc2hlCb5PBXlP/ogdysSJEj7ACID7RgPOi1Czvu0qqKpf/7HSlCgP9SicXgdNm7DZYheqHMA0GCSqGSIb3DQEBCwUAA4ICAQCM9B+Q0Vov1hYSzLQVQhh5/H97qQ+JS+AFf+D7srSe/zQ7EaSYwMsJNMSYxkhw80eqeWI2nDSFMJMu2w4kwtsQZ23rDBnQYS11Gri6buXtWZ2+toCRDeOzn502peBBBZKtnDhuy6AQfqTyEt8j6VZB1ojJ8YQ57dVtmVvex1XfkbzpcfuPNZajGHfzvDnkKI7wnt2W2+QA0cVXgKxwqEINTXr4CE/1qSxXZsjeiEAdn1MEhMyepkj98xIE5H4+RE9lZzOkStK4cZm3oL+8EP9E2LUkV+OEoVKUzAPTd894jOZfGj+mGbfZWSGNzDaDZO845cTVBdWUsGtMYyQ6GFUVmSpbtWv7Tu+0RhhSMr43FVz/Sz7SZ2BrV7TBdqV6He+AhsyYNZevgr0LbW+lVMB95nQlm/lvq7PXOO5mFRbV8uRbJnWx4fsuW+PELu34l7fnoEktLTnQYnlX/ml5IgG6UlbFNokNo+ffzRWqTdGzUHYLNhNYCQ0A7VfSOcbJQRpw76N5eqBODbUsf0IHccolhG4ALJ9iGJQMMXDB5q/oR9qjKqkWng2w9cZP4cUl2WZBI/D8jS2C+ZURyd9EjF9BKRecSFBZQDRnbuTjb0xF99w+SpxJCX0UyJJRS9VSLpK0pdNwpHP/fIIfT4RIrF/UQu1RSVUKAtzh4n0mmcN2DQ==",
"caCertificates": []
}
Sign up
Already have an account? Login
Login to the community
No account yet? Create an account
Login or Create an Account:
Log in with your Customer Care credentialsor
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.